Initial Thought
While finding hacking resources from The Hacker Recipes to exploit ESC4. I found out an interesting project name Exegol, which aims to provide ‘Powerful hacking environments securely, easily, professionally’. Why not giving it a try, right?
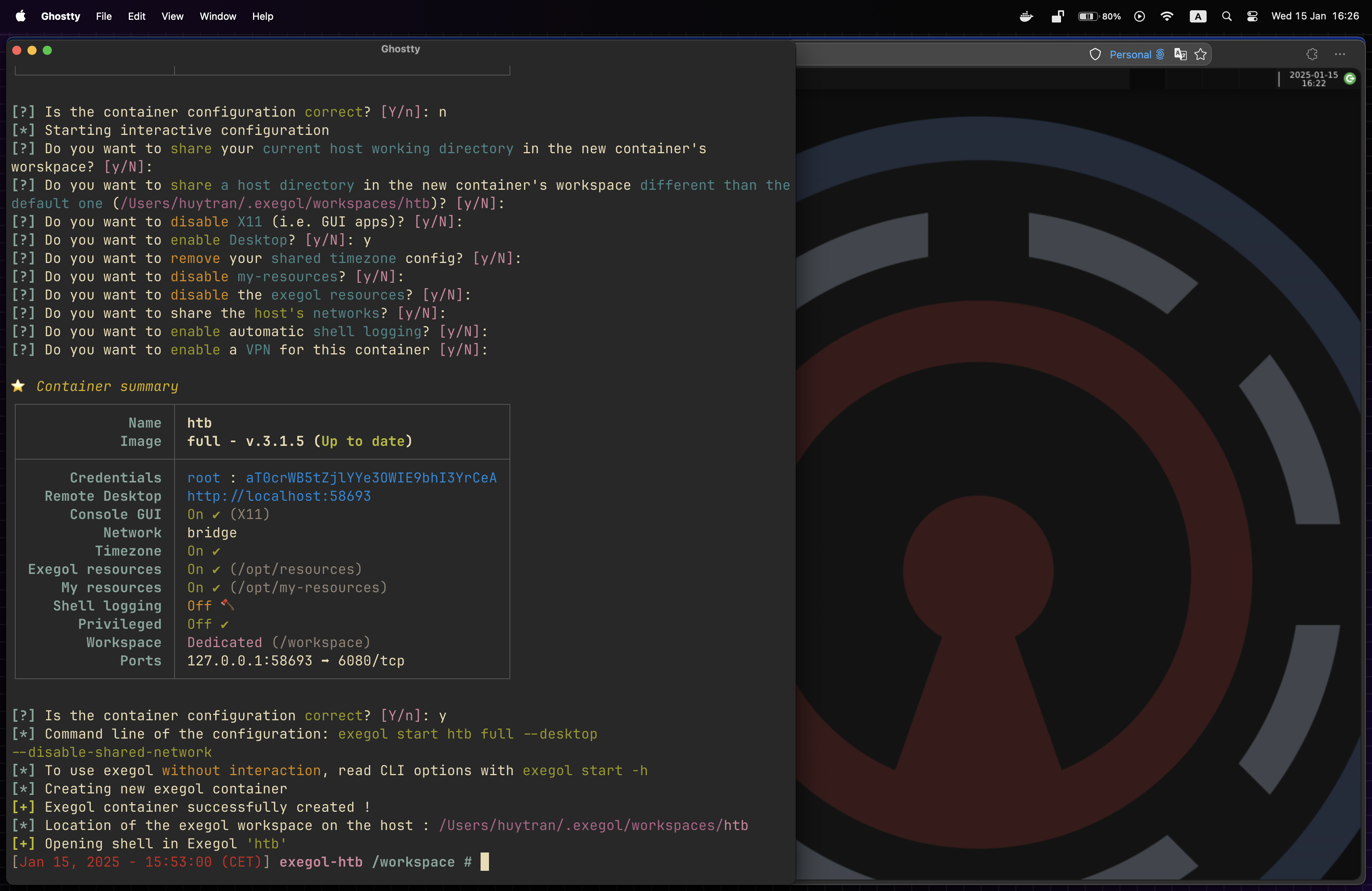
21/08/2025: I have completely removed Kali Linux from my setup due to the exceeded amount of storage it was using. It kept expanding in size and my computer could not keep up with it. So after the CPTS certification, I once again got back to Exegol, but now taking it seriously.
Exegol now maintaining a hybrid free/paid models, where:
- Community tier remains free for learners, the curious, and CTF players
- Pro and Enterprise tiers for commercial use, premium features, and direct support
Indeed, I support their decision, it means the tool will receive more attention. Which can lead to more frequent updates, more features, and hopefully less bugs.
What I don’t really like about Exegol is the lacking of sharing clipboard, I find it a bit annoy when I need extra step just to copy and paste from/to somewhere else.
I figured out that I can configure desktop to use VNC instead of HTTP, therefore the GUI is better now, with clipboard of course.
Adjustments
Resolve issue with alias
As I understand, most applications here run as an alias, and aliases only exist in your interactive shell, so Sliver (and other non-interactive processes) can’t see them. So, when I tried to run generate stager in Sliver C2:
[server] sliver > generate stager --lhost 10.10.10.10 --lport 4443 --format csharp --save staged.txt
[!] Error: rpc error: code = Unknown desc = msfvenom not found in PATH - Please make sure Metasploit framework >= v6.2 is installed and msfvenom/msfconsole are in your PATHThe workaround method I can think of is to create a wrapper script for msfvenom and msfconsole (just in case):
sudo tee /usr/local/bin/msfvenom >/dev/null <<'EOF'
#!/usr/bin/env bash
export BUNDLE_GEMFILE=/opt/tools/metasploit-framework/Gemfile
exec /usr/local/rvm/gems/ruby-3.1.5@metasploit-framework/wrappers/bundle exec /opt/tools/metasploit-framework/msfvenom "$@"
EOF
sudo chmod +x /usr/local/bin/msfvenomsudo tee /usr/local/bin/msfconsole >/dev/null <<'EOF'
#!/usr/bin/env bash
export BUNDLE_GEMFILE=/opt/tools/metasploit-framework/Gemfile
exec /usr/local/rvm/gems/ruby-3.1.5@metasploit-framework/wrappers/bundle exec /opt/tools/metasploit-framework/msfconsole "$@"
EOF
sudo chmod +x /usr/local/bin/msfconsole# Refresh the shell's command cache
hash -rBy adding real scripts in /usr/local/bin (which is already in your PATH), Sliver will successfully detect and invoke msfvenom and msfconsole.
[server] sliver > generate stager --lhost 10.10.10.10 --lport 4443 --format csharp --save staged.txt
[*] Sliver implant stager saved to: /workspace/staged.txtFreeRDP issue
I have not figured out the reason yet, but FreeRDP does not works for me when I used it directly from my MacOS terminal:
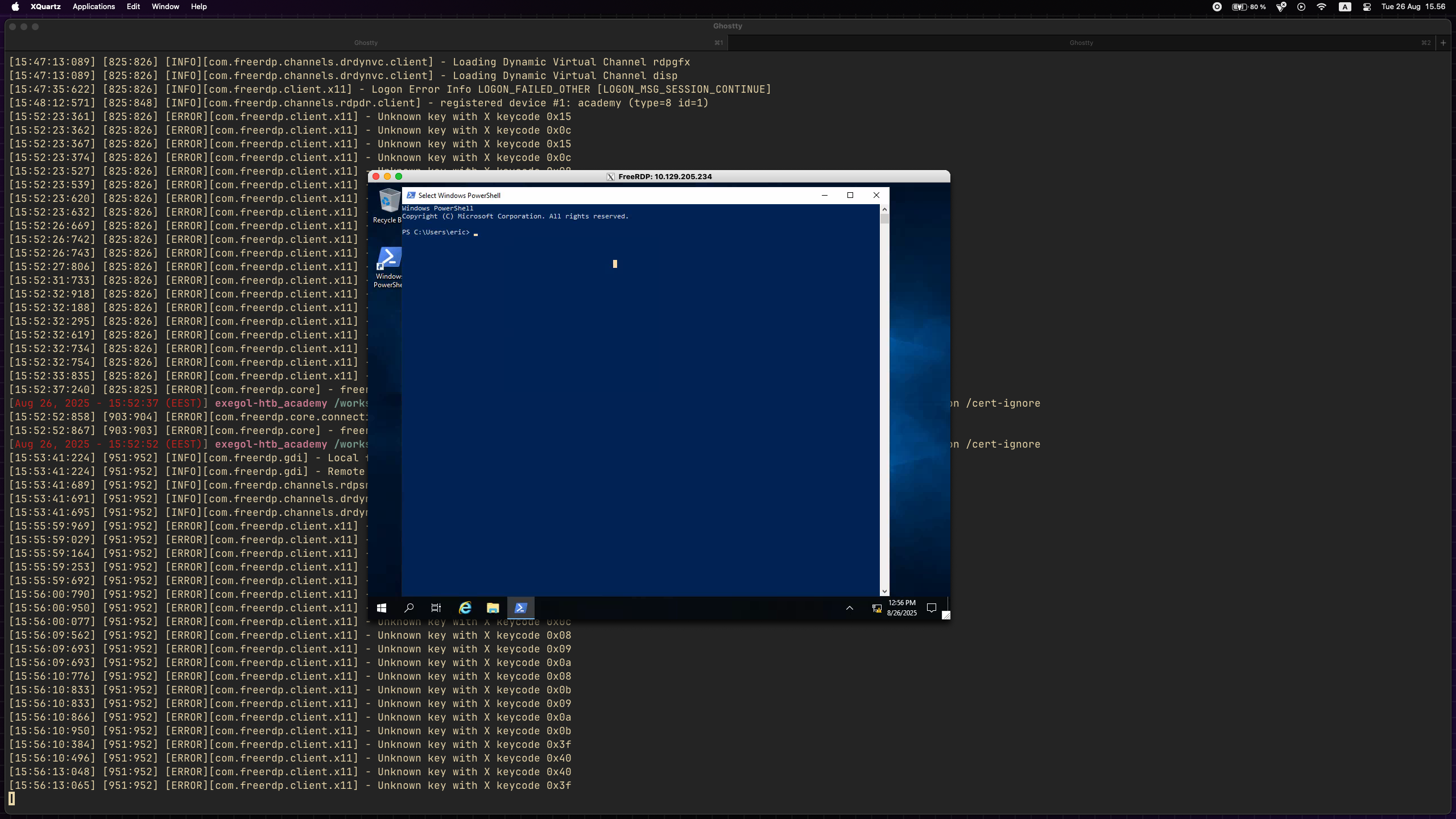
My solutions:
- Access Desktop mode using VNC (Better performance than Browser + HTTP)
- Use
rdesktop(haven’t checked this one)
Solution I got from Discord:
setxkbmap -rules base -model macintosh_old -layout usUpdate Containers
You cannot update your actual container in free version, you need to delete and recreate one:
- Delete your containers with
exegol remove CONTAINER_NAME - Update image with
exegol update free - Create a new container with updated image
exegol start
Back up any data that is not yet in /workspace, and if you want to keep the /workspace make sure to keep in when asked when removing the container (default choice is keeping it)